Si bien las medidas de aislamiento social se han relajado en diversos países, el cambio en los hábitos de uso de las herramientas financieras ha generado un pico estadístico de fraude alrededor del mundo. En este contexto, debe ser responsabilidad tanto de los proveedores de servicios financieros como de los usuarios construir una banca digital más segura con una “mayor cultura del riesgo digital”.
La última Encuesta mundial sobre delitos y fraudes económicos 2020 de PwC, indicó que el 47% de los encuestados sufrieron de fraude en los últimos 24 meses, lo que incluye el periodo de enero a junio de 2020, donde se registró un aumento del 70% en los ataques.
Esto, explica la consultora PwC, se debe a que el fraude suele ser más extensivo durante las crisis y recesiones, y ambos están ocurriendo con la pandemia del COVID-19. Solo que ahora los medios de pago más usados son los digitales y es allí donde los cibercriminales concentran sus esfuerzos.
Modalidad de fraude más popular
El mismo informe señala que la modalidad de fraude más popular es el “phishing” o correo malicioso. Se trata de una técnica de engaño, que a través de un correo electrónico o una página web falsa extrae los datos privados de los usuarios, especialmente datos bancarios. Un ejemplo de “phishing” es la supuesta compra de un artículo por una página de comercio electrónico, que en realidad solo toma los datos de pago de los usuarios, para luego hacer fraude con estos.
Se trata de dos de los fraudes más habituales hoy día. El ataque de ‘phishing’ viene por medio de un correo electrónico en el que se pide al cliente sus datos de cuenta y clave de acceso, simulando la página legítima del comercio o entidad para que los usuarios brinden claves personales o información sobre tarjetas de crédito.
Por otro lado, el ‘smishing’ es una variable del ‘phishing’ y es un tipo de delito que emplea mensajes de texto dirigidos a usuarios de telefonía móvil con intención de estafar, mediante reclamos atractivos con alertas urgentes, ofertas interesantes o grandes premios, con los que tratan de engañar al usuario, aprovechando las funcionalidades de navegación web que incorporan los dispositivos móviles actuales.
El objetivo es conseguir que el usuario o víctima realice una acción en beneficio del estafador para que suministre información sensible como sus datos personales. El éxito de este fraude depende principalmente del nivel de conocimiento de la persona a la que quieren robar y de otras circunstancias como el descuido que pueda tener en
Google typically sees somewhere around 240 million spam messages every day. But, last week, the company announced that more than 18 million scheme emails specifically related to COVID-19 went out every single day. The messages were mostly typical phishing schemes—trying to get users to click a link and provide personal information—just updated with new coronavirus-related text.
Some of the messages claim to come from employers, which is particularly effective in a time when so many workers are spread out in remote locations. The messages can also mimic those from health professionals, government agencies, or school districts.
4. Tech support scams
You’re bound to run into tech problems working from home. Since you probably don’t want experts inside your home to fix the problem, you may be at the mercy of online or telephone tech support. Do not Google search a company’s tech support line. Scammers are hoping you’ll do just that and fall into their trap.
Make sure the number you dial is the real number. Go to the company’s official web site and get the phone number from the Contact Us section. There are lots of phishing schemes out there, designed by hackers who want to access personal information and commandeer your network.
A caller to my national radio show fell for this scam and he owns a Homeland Security company. Tap or click here to learn his four chilling lessons from a tech support hotline scam.
Sextortion scams
With so many people communicating through Zoom and other video chats, we are now relying on our webcams more than ever. Be mindful of any webcam you own, and consider covering it up when it’s not in use. A piece of black electrical tape works well.
You might get an email with a subject line that contains your password. When you open the email, a threatening message claiming to be from a hacker says that your webcam has been compromised and that they’ve caught you in a moment of intimacy. Now, it’s time to pay up in Bitcoin, or else the hacker will expose you publicly.
That password is one compromised in a data breach. Don’t pay the hacker. Delete the email and if you’re still using the same password at different sites, change it now.
Government-issued online coronavirus tests
Coronavirus tests are in short supply, and many people are eager to find one. The Food and Drug Administration recently approved the first at-home test, a nasal swab said to be safe and accurate. That said, if you find a vendor selling “coronavirus tests” online, this is almost certainly a scam. You should always consult a physician before taking the test and follow the instructions closely.
When people are away from the office, they are more susceptible to business email compromise and other social engineering attacks.
“The hacker pretends to be the company’s CEO or another employee and tricks the person into conducting a wire transfer or sharing online credentials,” Glassberg said. “I have no doubt we are going to see data breaches and wire transfer fraud as a result of this outbreak.”
The most common type of attack is a phishing-style cyberattack where an attacker sends an email to a remote workforce while pretending to be their IT manager, said Arun Kothanath, chief security strategist at Clango, a cybersecurity advisory firm in Arlington, Virginia. The email will typically ask employees to sign in to an online portal using their credentials to ensure they still have access to a business-critical resource.
“Attackers will capture those credentials and then can move laterally and vertically throughout an organization until they capture the data or access they desire,” he said. “Organizations without a privileged access management program that can recognize and terminate abnormal identity-behavior will be especially vulnerable to this type of attack.”
Another type of cyberattack that has become more frequent in recent weeks is a social engineering cyber attack. This is where an attacker, masquerading as a frustrated remote employee who cannot access business-critical systems, will contact an IT administrator or help desk technician and request access to sensitive data, infrastructure or assets, Kothanath said.
identifica Phishing:
- Look at the «from» field. Is the person or business’s name spelled correctly, and does the email address actually match the name of the sender? Or are there a bunch of random characters in the email address instead?
- While we’re at it, does the email address seem close, but a little off? E.g. Microsft.net, or Microsoft.co.
- Hover your mouse over any links in the email to see the true URLs they will send you to. Do they look legitimate? Remember not to click!
- Check the greeting. Does the sender address you by name? «Customer» or «Sir» would be red flags.
- Read the email closely. Is it generally free from spelling errors or odd grammar?
- Think about the tone of the message. Is it overly urgent or trying to get you to do something you normally wouldn’t?
The Nigerian scam
Probably one of the oldest and most popular Internet scams used mostly by a member of a Nigerian family with wealth to trick different people. It is also known as “Nigerian 419”, and named after the section of Nigeria’s Criminal Code which banned the practice.
A typical Nigerian scam involves an emotional email, letter, text message or social networking message coming from a scammer (which can be an official government member, a businessman or a member of a very wealthy family member – usually a woman) who asks you to give help in retrieving a large sum of money from a bank, paying initially small fees for papers and legal matters. In exchange for your help, they promise you a very large sum of money.
They will be persistent and ask you to pay more and more money for additional services, such as transactions or transfer costs. You’ll even receive papers that are supposed to make you believe that it’s all for real. In the end, you are left broke and without any of the promised money.
6. Hitman scam
One of the most frequent Internet scams you can meet online is the “hitman” extortion attempt. Cybercriminals will send you an email threatening to extort money from you. This type of online scam may come in various forms, such as the one threatening that they will kidnap a family member unless a ransom is paid in a time frame provided by the scammers.
To create the appearance of real danger, the message is filled with details from the victim’s life, collected from an online account, a personal blog or from a social network account.
That’s why it’s not safe to provide any sensitive or personal information about you on social media channels. It might seem like a safe and private place, where you’re only surrounded by friends, but in reality, you can never know for sure who’s watching you.
Also, it’s better to be a little bit paranoid and protect all your digital assets like everyone is watching. Here’s how a Hitman scam looks like:
Fake shopping websites
We all love shopping and it’s easier and more convenient to do it on the Internet with a few clicks. But for your online safety, be cautious about the sites you visit. There are thousands of websites out there that provide false information and might redirect you to malicious links, giving hackers access to your most valuable data.
If you spot a great online offer which is “too good to be true”, you might be tempted to say “yes” instantly, but you need to learn how to spot a fake shopping site so you don’t get scammed.
We strongly recommend reading these online shopping security tips to keep yourself safe from data breaches, phishing attacks or other online threats.
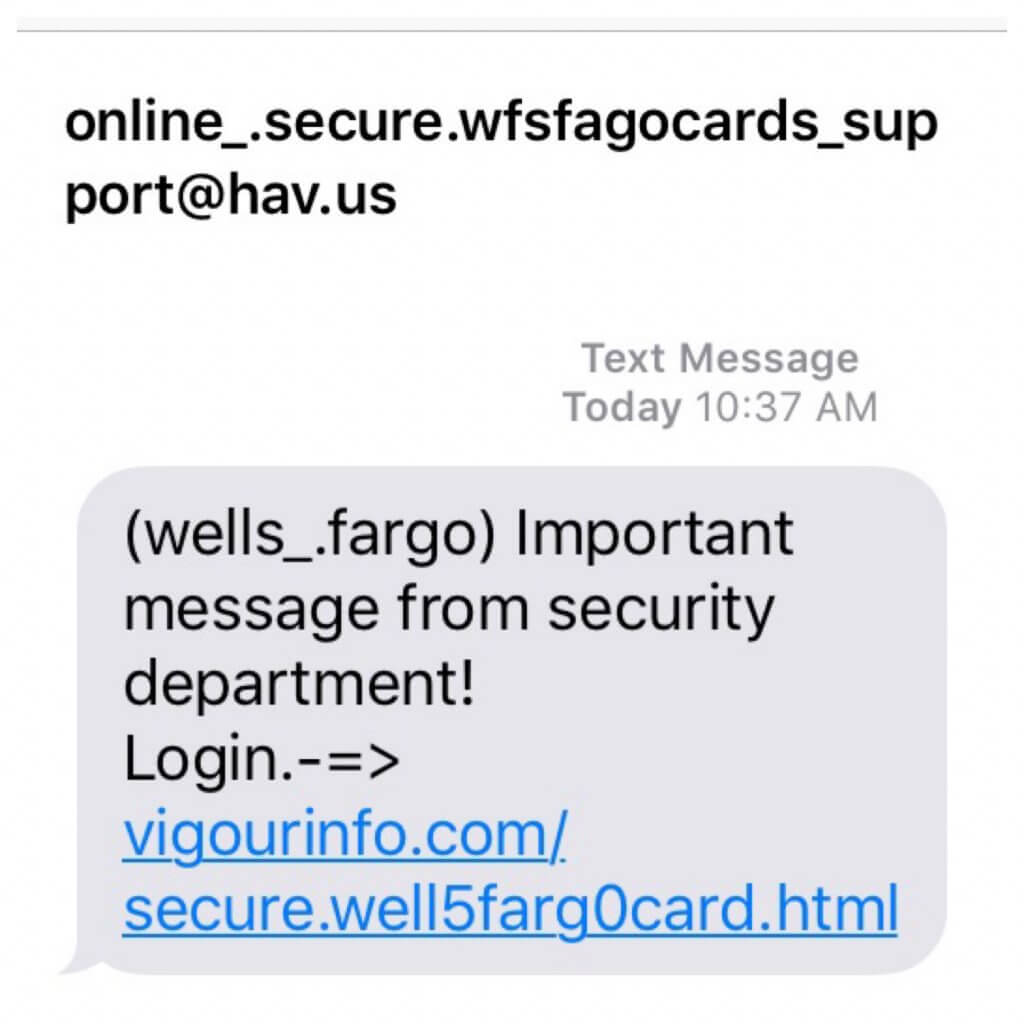
17. SMS Scaming (Smshing)
Smartphones. You can’t live without them in the era of the Internet. They’ve become essential for communication, online shopping, banking or any other online activity.
Needless to say the amount of data we store on our personal devices which make them vulnerable to cybercriminals, always prepared to steal our online identities or empty our bank accounts.
Smishing (using SMS text messages) is a similar technique to phishing, but, instead of sending emails, malicious hackers send text messages to their potential victims.
How does this happen? You receive an urgent text message on your smartphone with a link attached saying that it’s from your bank and you need to access it in order to update your bank information or other online banking information.
Be careful about these SMS you receive and don’t click on suspicious links that could redirect to malicious sites trying to steal your valuable data. These useful tips can help you easily spot these types of online scams.
Chain Letters
You’ve likely seen this one before — the dreaded chain letter has returned. It may appear in the form of, «Retweet this and Bill Gates will donate $5 million to charity!» But hold on, let’s think about this. Bill Gates already does a lot for charity. Why would he wait for something like this to take action? Answer: He wouldn’t. Both the cause and claim are fake.

So why would someone post this? Good question. It could be some prankster looking for a laugh, or a spammer needing «friends» to hit up later. Many well-meaning people pass these fake claims onto others. Break the chain and inform them of the likely ruse.
4. Cash Grabs
By their very nature, social media sites make it easy for us to stay in touch with friends, while reaching out to meet new ones. But how well do you really know these new acquaintances? That person with the attractive profile picture who just friended you — and suddenly needs money — is probably some cybercriminal looking for easy cash. Think twice before acting. In fact, the same advice applies even if you know the person.
Picture this: You just received an urgent request from one of your real friends who «lost his wallet on vacation and needs some cash to get home.» So, being the helpful person you are, you send some money right away, per his instructions. But there’s a problem: Your friend never sent this request. In fact, he isn’t even aware of it. His malware-infected computer grabbed all of his contacts and forwarded the bogus email to everyone, waiting to see who would bite.
Again, think before acting. Call your friend. Inform him of the request and see if it’s true. Next, make sure your computer isn’t infected as well.
3. Hidden Charges
«What type of STAR WARS character are you? Find out with our quiz! All of your friends have taken it!» Hmm, this sounds interesting, so you enter your info and cell number, as instructed. After a few minutes, a text turns up. It turns out you’re more Yoda than Darth Vader. Well, that’s interesting … but not as much as your next month’s cell bill will be.
You’ve also just unwittingly subscribed to some dubious service that charges $9.95 every month.
As it turns out, that «free, fun service» is neither. Be wary of these bait-and-switch games. They tend to thrive on social sites.
2. Phishing Requests
«Somebody just put up these pictures of you drunk at this wild party! Check ‘em out here!» Huh? Let me see that! Immediately, you click on the enclosed link, which takes you to your Twitter or Facebook login page. There, you enter your account info — and a cybercriminal now has your password, along with total control of your account.
How did this happen? Both the email and landing page were fake. That link you clicked took you to a page that only looked like your intended social site. It’s called phishing, and you’ve just been had. To prevent this, make sure your Internet security includes antiphishing defenses. Many freeware programs don’t include this essential protection.
1. Hidden URLs
Beware of blindly clicking on shortened URLs. You’ll see them everywhere on Twitter, but you never know where you’re going to go since the URL («Uniform Resource Locator,» the Web address) hides the full location. Clicking on such a link could direct you to your intended site, or one that installs all sorts of malware on your computer.
URL shorteners can be quite useful. Just be aware of their potential pitfalls and make sure you have real-time protection against spyware and viruses.
Bottom line: Sites that attract a significant number of visitors are going to lure in a criminal element, too. If you take security precautions ahead of time, such as using antivirus and anti-spyware protection, you can defend yourself against these dangers and surf with confidence.